Our Approach
Using our 5-step security management process, we create a virtuous cycle for developing effective,
scalable cybersecurity programs that match the unique needs of our clients.
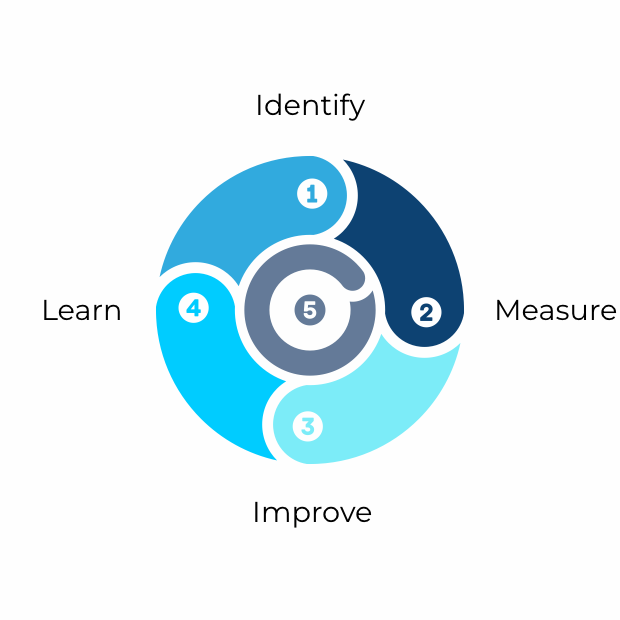
Our 5-Step Process
We take a pragmatic approach to cybersecurity that balances security, complexity, and cost to find the optimal level of protection given each client’s environment, experience, and budget. We design structured security programs and solutions appropriate to each organization’s size, technology, and level of security expertise.
Our ultimate goal is to empower our clients by making them more knowledgeable and self-sufficient. We accomplish this by helping every client build a cohesive security program that incorporates awareness of potential threats, knowledge of appropriate defenses and countermeasures, visibility into security events, and the understanding to build systems and software resilient to current and future threats.
Our process involves five steps that together form a virtuous security cycle: Identify, Measure, Improve, Learn, and Repeat.
5 Steps to Highly Effective Security

Step 1: Identify
Find vulnerabilities and weaknesses in networks, hosts, devices, services, and applications. Review security policies, procedures, tools, and controls for oversights, omissions, and misconfigurations.
Step 2: Measure
Actively probe and exploit discovered vulnerabilities to measure their true impact on infrastructure, system, and personnel security. Assign actionable metrics for prioritization and resolution of discovered vulnerabilities.

Step 3: Improve
Review findings and craft a plan to remediate or mitigate findings through best-practice security design and architecture, configuration management, and secure software development principles.

Step 4: Learn
Review corrective measures with stakeholders, educate technical and nontechnical staff, and incorporate learnings into policies, procedures, and security controls.

Step 5: Repeat
Periodically repeat steps 1-4 to ensure an up-to-date and effective security program. Incorporate learnings into future planning and execution efforts.
Identify
We start by identifying weaknesses in infrastructure, services, applications, and procedures. We use a variety of methods including threat modeling, vulnerability assessments, structured checklists and questionnaires, design and architecture reviews, and source code analysis to pinpoint vulnerabilities, misconfigurations, architectural flaws, and insecure code.

- Threat modeling
- Vulnerability assessment
- Security tools and controls review
- Security policy and procedure review
- Regulatory compliance checks
- Source code review
Measure
With an understanding of the attack surface for your environment, we actively exploit discovered vulnerabilities to determine your true level of exposure. This step tests defense-in-depth strategy, identifies dangerous interdependencies, exercises monitoring and alerting capabilities, and highlights gaps in security awareness. We accomplish this through penetration testing, cooperative attack-response exercises, and social engineering.
- Penetration testing
- Application security testing
- Attack-response exercises
- Social engineering
Improve
Based on the outcome of steps 1 and 2, we make recommendations for improving your overall security posture. We provide guidance on patching and hardening vulnerable systems, securing networks and cloud services, and developing and deploying secure applications. We achieve this through robust configuration management, proven secure software development lifecycle practices, and security design and architecture services.

- Configuration management best practices
- Security design and architecture
- Cloud infrastructure
- Web and mobile applications
- Microservices and APIs
- Data storage and processing systems
- Secure software development lifecycle
- Application security best practices
- Security system development
- Secure CI/CD
Learn
Armed with the knowledge of vulnerabilities, exposure, and controls and countermeasures from steps 1-3, we educate our clients on the security practices that matter most given their particular environment and circumstances. We do this through in-depth assessment review, security deep dives, and security awareness training.

- Post-assessment analysis
- Subject matter deep dives
- Group security Q&A
- Organization-wide security awareness training
Repeat
Security is not a one-and-done affair. Technology evolves, attackers adapt, and threats change. To keep ahead of the threats, you must regularly re-revisit steps 1-4 to ensure up-to-date and effective security controls. Not only does this keep your environment current, but it fosters a culture of proactive planning and security awareness. The final step in our methodology provides a feedback loop for continuous improvement.

